Contents
Dynamic Business’s Tech Tuesdays column is devoted to the enterprises and products and solutions that have designed good contributions to the tech field, are pushing the boundaries of technology, and are redefining the upcoming.
For this week’s edition, we’ve place jointly a listing of noteworthy improvements in company security that can really enable you safe your digitisation agenda in 2022 and outside of.
YubiKey Bio Sequence
The YubiKey Bio Series is the very first YubiKey collection that supports fingerprint recognition for secure password-significantly less and next-issue logins. It has been formulated by Yubico, the leading supplier of components authentication security keys.
The YubiKey Bio allows you to securely log into on the internet accounts without having the need to have for a password. Crafted for biometric authentication on desktops, the YubiKey Bio Series supports fashionable FIDO2/WebAuthn and U2F protocols, in the two USB-A and USB-C kind variables.
In keeping with Yubico’s innovation and layout, the YubiKey Bio does not demand any batteries, drivers, or associated software program. The new security keys combine with the indigenous biometric enrolment and administration functions supported in the most current platforms and working units.
The YubiKey Bio launched in October last year and is available for order on yubico.com at a retail selling price of US$80 for the USB-A type-issue and US$85 for the USB-C sort-element.
PhishER™ from KnowBe4
With automatic prioritisation for emails, PhishER™ allows your InfoSec and Safety Operations workforce slash by means of inbox sound and reply to the most perilous threats a lot more rapidly.
PhishER is the important component of an essential security workstream. It’s your light-weight Protection Orchestration, Automation and Response (SOAR) system to orchestrate your danger reaction and control the high volume of most likely destructive e mail messages described by your end users. With automatic prioritisation of e-mail, PhishER allows your crew slash via the inbox sounds and respond to the most harmful threats a lot more rapidly.
Additionally, with PhishER you are able to automate the workstream of the 90% of claimed e-mail that are not threats. Incident Reaction (IR) orchestration can easily produce speedy efficiencies to your protection staff, but the possible price is a great deal better than that.
PhishER is at this time accessible as a stand-by itself item or as an increase-on choice for present-day KnowBe4 prospects.
Read far more on it in this article – PhishER | KnowBe4
Vacation Help App and Portal
Entire world Travel Protection’s Travel Assist App and Portal work together to provide business travellers and travel professionals with the details and guidance they need at their fingertips. It provides together leading technology and trustworthy, verified intelligence providers to supply travellers with a greatest-in-field global journey chance administration resource.
The portal enables selection-makers to act promptly and travellers to really feel supported – specific and actionable intelligence run by AI intelligence. It also offers the accuracy, expertise and technology needed to handle secure journey. Its extremely customisable AI in addition to analyst-driven information and facts – customise travel and itinerary monitoring, privacy and locale ghosting, maps and alerts dependent on travellers and services.
It also permits speaking with travellers by way of the chat dashboard and emergency disaster button that phone calls specifically to Globe Journey Protection’s clinical and security gurus.
For further more details: https://worldtravelprotection.com/products and services/journey-possibility-administration-equipment/
BeyondTrust Privileged Distant Access
BeyondTrust Privileged Distant Access controls accessibility to critical programs and remote desktops with no hindering the work users require to conduct. Businesses can intently determine how users join, check sessions in authentic-time, and file each individual session for a in depth audit path. In the meantime, close-customers, no matter whether workforce or third-get together contractors, get a simple, straightforward-to-use console.
BeyondTrust Privileged Remote Obtain 22.2 was introduced in June 2022 and even further supports customers to enforce a policy of the very least privilege by supplying users just the ideal degree of access wanted for their roles. For shared accounts, organizations can simply set up person person accountability, outline what endpoints consumers can obtain, routine when they can obtain them, and whitelist/blacklist applications for a thorough solution to privileged entry.
Administrators and IT groups can consolidate the monitoring, approval, and auditing of privileged accounts in just one position. Privileged Remote Accessibility makes it possible for these hugely interconnected qualifications to be vaulted and makes rotation achievable, greatly increasing an organisation’s security posture.
Here’s extra: https://www.beyondtrust.com/remote-accessibility
Palo Alto Networks PA-410
Organizations of all measurements are adopting cloud and mobility technologies to develop into a lot more agile, and impressive and offer a improved personnel knowledge.
Released in Australia in September 2021, the PA-410 employs offers the exact gains as Palo Alto Networks’ larger device finding out-driven Future-Era Firewall merchandise, in a deal that is additional ideal for SMBs or organization branch destinations. With it, businesses can halt threats in serious-time, protected community traffic without slowing down small business, and enable Zero Belief Network Security with negligible upkeep.

Listed here’s more.
LogRhythm SIEM Platform edition 7.9
LogRhythm SIEM System edition 7.9 allows enterprises enhance protection workflow, cut down their cybersecurity exposure, do away with blind spots across the IT environment, shut down assaults and restrict destruction and disruption.
Essential features involve log management which enables customers to swiftly look for across their organisation’s huge information to effortlessly discover answers, discover IT and stability incidents, and swiftly troubleshoot challenges. In addition, superior equipment analytics permits businesses to precisely detect destructive activity by security and compliance use scenario content material and threat-primarily based prioritised alarms that straight away floor critical threats.
Users can also detect anomalous consumer behaviour ahead of data is corrupted or exfiltrated with user and entity conduct analytics. Finally, consumers can collaborate, streamline, and evolve their team’s safety maturity with safety orchestration, automation, and reaction (SOAR) that is embedded in the LogRhythm SIEM and integrates with extra than 80 spouse remedies to help risk checking, looking and investigation.
LogRhythm 7.9 is offered from LogRhythm Australian Solutions Approved Companions.
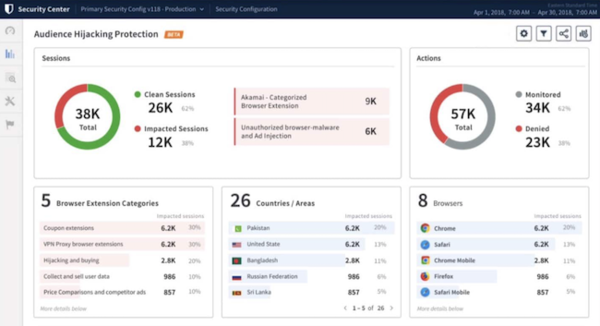
Viewers Hijacking Protector
Audience Hijacking Protector is a new solution designed for online organizations to maximise earnings opportunities and minimise advertising fraud in the obtaining journey. As the pace of on the internet retail raises, stability groups for online brands are going through a new prevalent, shopper-side phenomenon.
Acknowledged as audience hijacking, shops are grappling with a escalating challenge the place unauthorised ads and pop-ups lure buyers absent from online outlets – disrupting customer activities and leading to lost earnings
To master extra about Akamai’s Viewers Hijacking Protector and other products and solutions and abilities that empower shoppers to provide steady on-line encounters, visit https://www.akamai.com/items.
Arlo Go 2 4G + WIFI Mobile Stability Camera
Utilizing a 4G mobile information strategy by means of SIM, the Arlo Go 2 provides ongoing connectivity and uninterrupted protection. Businesses can perspective and history 1080p comprehensive Hd online video day and night time, as very well as seize vital facts with color evening eyesight many thanks to an built-in highlight.
Arlo Go 2 is equipped with GPS positioning to observe the camera’s whereabouts, allowing buyers to track down multiple units across an expansive place, or in the party of theft.
The Arlo Go 2 includes obtain to Arlo Safe, Arlo’s AI-subscription assistance, by means of a complimentary demo. The company grants end users entry to rolling 30-day cloud recording, and personalised notifications such as a man or woman, animal, auto and package detection. The camera’s versatility not only presents users with peace of mind that their assets and property are safe, but is underscored by a 100% wire-free, temperature-resistant style and design, a swappable, rechargeable battery, and the means to straight connect to Wi-Fi when in vary.
The Arlo Go 2 4G + Wi-Fi Protection Digicam is now offered nationwide through arlo.com and taking part stores at an RRP of $429 AUD.
SureDrop, a resolution by Senetas is the only totally showcased file-sharing and collaboration application developed from the ground up as a cybersecurity option. It is utilized by corporations and authorities organisations such as AUCloud.
SureDrop
SureDrop provides superior encryption and file fragmentation in addition to quite a few person protection options, which includes seamless integration with enterprise and company purposes – Microsoft 365, Outlook, Azure and Active Directory.
It gives facts sovereignty handle and supports ‘certified’ cloud sovereign knowledge storage which is often essential by governments. SureDrop also delivers Votiro Cloud API – a exceptional feature that offers the most state-of-the-art safeguarding in opposition to ransomware and malware.
CEO of Senetas, Andrew Wilson states, “Remote work is here to stay, but it is also presenting several options for malicious actors. Sharing particular and monetary facts in excess of electronic mail is commonplace in legal, accounting and mortgage loan broking products and services all over the entire world, with the security of that details typically currently being an afterthought.”
For far more information: https://www.suredrop.io/
CylanceGUARD
Corporations of all dimensions are challenged to install guidelines and secure info on a developing selection of devices, primary to an enhanced quantity of alerts to manage.
To help solve this, BlackBerry offers CylanceGUARD, an on-demand, 24/7/365 Managed Extended Detection and Reaction (XDR) support that takes advantage of the prediction advantage of Artificial Intelligence (AI) to detect or remediate threats right before they bring about problems.
Out there on a subscription, it is significantly interesting for SMBs who advantage from company-quality cybersecurity resources and guidance, at a fraction of the price tag.
CylanceGuard is accessible to Australian organizations by using a quantity of our MSSP companions in two distinct offers, CylanceGUARD and CylanceGUARD Advanced, made to meet up with any business’s requirements.
Extra listed here.


