Contents
Dynamic Business’s Tech Tuesdays column is dedicated to the corporations and items that have designed excellent contributions to the tech market, are pushing the boundaries of technology, and are redefining the upcoming.
For this week’s version, we’ve put alongside one another a listing of notable improvements in small business safety that can seriously assist you protected your digitisation agenda in 2022 and over and above.
YubiKey Bio Collection
The YubiKey Bio Collection is the initially YubiKey collection that supports fingerprint recognition for safe password-fewer and second-issue logins. It has been developed by Yubico, the major provider of components authentication stability keys.
The YubiKey Bio makes it possible for you to securely log into on the internet accounts with out the need to have for a password. Designed for biometric authentication on desktops, the YubiKey Bio Series supports fashionable FIDO2/WebAuthn and U2F protocols, in each USB-A and USB-C sort variables.
In retaining with Yubico’s innovation and design, the YubiKey Bio does not require any batteries, drivers, or associated application. The new stability keys combine with the native biometric enrolment and administration features supported in the most up-to-date platforms and operating methods.
The YubiKey Bio launched in October previous 12 months and is available for order on yubico.com at a retail price tag of US$80 for the USB-A form-aspect and US$85 for the USB-C form-variable.
PhishER™ from KnowBe4
With automatic prioritisation for email messages, PhishER™ can help your InfoSec and Protection Operations team slash as a result of inbox sound and respond to the most perilous threats more promptly.
PhishER is the vital component of an crucial protection workstream. It is your lightweight Safety Orchestration, Automation and Reaction (SOAR) system to orchestrate your danger reaction and regulate the substantial quantity of probably malicious e mail messages claimed by your consumers. With automated prioritisation of e-mails, PhishER allows your team slice by the inbox sound and reply to the most dangerous threats far more immediately.
Furthermore, with PhishER you are capable to automate the workstream of the 90% of reported e-mails that are not threats. Incident Response (IR) orchestration can effortlessly deliver quick efficiencies to your protection team, but the possible worth is much bigger than that.
PhishER is now available as a stand-alone products or as an include-on alternative for current KnowBe4 consumers.
Study more on it listed here – PhishER | KnowBe4
Travel Help Application and Portal
Earth Journey Protection’s Travel Assist App and Portal work collectively to deliver business enterprise travellers and travel administrators with the information and facts and help they need to have at their fingertips. It provides collectively leading technology and reputable, verified intelligence companies to give travellers with a very best-in-industry world wide travel risk administration instrument.
The portal enables determination-makers to act promptly and travellers to come to feel supported – qualified and actionable intelligence run by AI intelligence. It also provides the precision, knowledge and technology needed to control risk-free journey. Its really customisable AI in addition to analyst-driven details – customise journey and itinerary monitoring, privateness and area ghosting, maps and alerts based on travellers and services.
It also lets speaking with travellers by means of the chat dashboard and crisis crisis button that phone calls straight to Globe Travel Protection’s health-related and safety experts.
For additional data: https://worldtravelprotection.com/products and services/journey-danger-administration-applications/
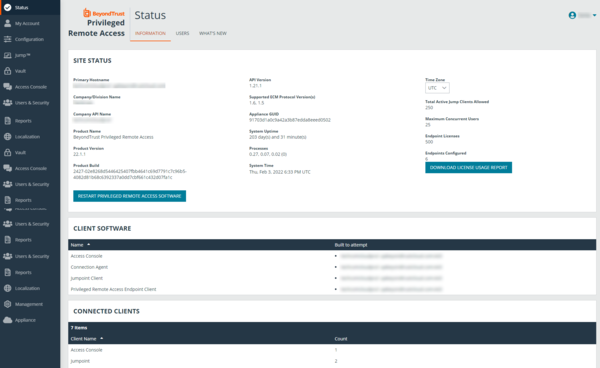
BeyondTrust Privileged Remote Entry
BeyondTrust Privileged Remote Access controls entry to crucial systems and distant desktops without hindering the do the job end users require to execute. Businesses can carefully outline how people connect, monitor classes in actual-time, and report every single session for a specific audit path. Meanwhile, stop-consumers, regardless of whether staff or 3rd-social gathering contractors, get a easy, straightforward-to-use console.
BeyondTrust Privileged Remote Obtain 22.2 was launched in June 2022 and even further supports clients to enforce a policy of the very least privilege by giving customers just the correct degree of accessibility essential for their roles. For shared accounts, businesses can effortlessly build particular person user accountability, outline what endpoints consumers can access, schedule when they can entry them, and whitelist/blacklist apps for a extensive tactic to privileged obtain.
Administrators and IT groups can consolidate the tracking, acceptance, and auditing of privileged accounts in a person spot. Privileged Remote Entry enables these highly interconnected qualifications to be vaulted and makes rotation achievable, drastically growing an organisation’s protection posture.
Here’s much more: https://www.beyondtrust.com/remote-accessibility
Palo Alto Networks PA-410
Firms of all measurements are adopting cloud and mobility technologies to develop into additional agile, and impressive and give a much better staff encounter.
Launched in Australia in September 2021, the PA-410 makes use of presents the identical gains as Palo Alto Networks’ more substantial machine learning-driven Subsequent-Technology Firewall items, in a offer that’s extra acceptable for SMBs or organization department areas. With it, organizations can end threats in authentic-time, safe community targeted visitors without slowing down small business, and empower Zero Belief Community Protection with minimal maintenance.

Here’s more.
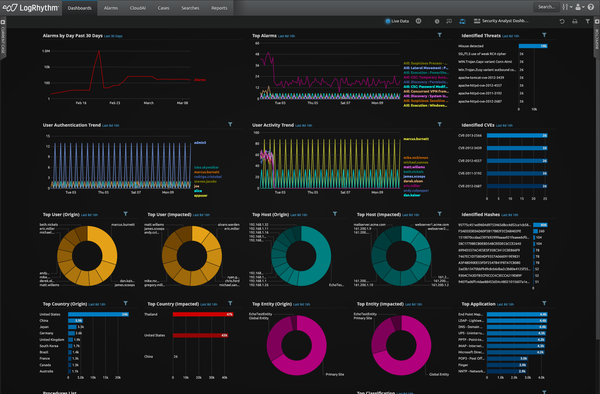
LogRhythm SIEM Platform edition 7.9
LogRhythm SIEM System model 7.9 assists corporations boost safety workflow, minimize their cybersecurity exposure, eliminate blind places across the IT environment, shut down assaults and limit injury and disruption.
Key options include things like log management which enables buyers to swiftly look for throughout their organisation’s large details to conveniently obtain responses, discover IT and stability incidents, and immediately troubleshoot troubles. In addition, superior machine analytics allows providers to correctly detect destructive exercise by way of security and compliance use situation written content and risk-centered prioritised alarms that immediately surface significant threats.
Users can also detect anomalous user behaviour right before knowledge is corrupted or exfiltrated with consumer and entity behaviour analytics. Finally, end users can collaborate, streamline, and evolve their team’s safety maturity with security orchestration, automation, and reaction (SOAR) that is embedded in the LogRhythm SIEM and integrates with additional than 80 partner options to aid risk checking, hunting and investigation.
LogRhythm 7.9 is available from LogRhythm Australian Products and services Licensed Partners.
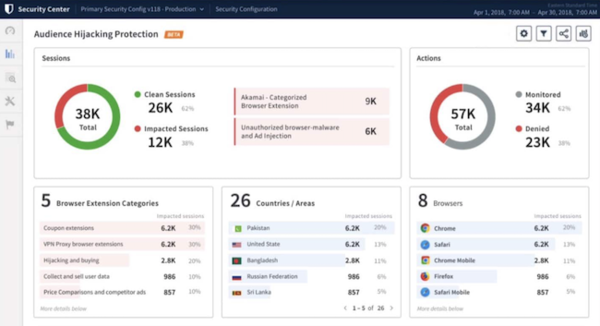
Audience Hijacking Protector
Viewers Hijacking Protector is a new option made for on the net enterprises to maximise revenue chances and minimise promoting fraud in the acquiring journey. As the pace of on the web retail will increase, security teams for on the web brand names are facing a new common, customer-side phenomenon.
Acknowledged as viewers hijacking, shops are grappling with a expanding dilemma the place unauthorised advertisements and pop-ups entice customers away from on line outlets – disrupting buyer encounters and leading to dropped earnings
To learn more about Akamai’s Audience Hijacking Protector and other items and abilities that empower prospects to present constant on the internet encounters, visit https://www.akamai.com/goods.
Arlo Go 2 4G + WIFI Mobile Security Digital camera
Working with a 4G cellular knowledge strategy by way of SIM, the Arlo Go 2 provides ongoing connectivity and uninterrupted security. Businesses can check out and file 1080p total Hd movie working day and evening, as perfectly as seize essential details with color evening eyesight thanks to an integrated spotlight.
Arlo Go 2 is geared up with GPS positioning to monitor the camera’s whereabouts, allowing for end users to identify multiple devices throughout an expansive spot, or in the function of theft.
The Arlo Go 2 includes accessibility to Arlo Secure, Arlo’s AI-membership support, by using a complimentary trial. The assistance grants people entry to rolling 30-working day cloud recording, and personalised notifications this kind of as a particular person, animal, automobile and package detection. The camera’s flexibility not only delivers consumers with peace of intellect that their residence and belongings are safe, but is underscored by a 100% wire-free of charge, temperature-resistant design, a swappable, rechargeable battery, and the skill to straight link to Wi-Fi when in range.
The Arlo Go 2 4G + Wi-Fi Protection Camera is now offered nationwide through arlo.com and collaborating vendors at an RRP of $429 AUD.
SureDrop, a resolution by Senetas is the only totally featured file-sharing and collaboration software intended from the floor up as a cybersecurity alternative. It is utilized by firms and federal government organisations together with AUCloud.
SureDrop
SureDrop provides highly developed encryption and file fragmentation in addition to various user safety characteristics, such as seamless integration with enterprise and company applications – Microsoft 365, Outlook, Azure and Energetic Directory.
It supplies info sovereignty management and supports ‘certified’ cloud sovereign facts storage which is usually necessary by governments. SureDrop also provides Votiro Cloud API – a unique attribute that provides the most sophisticated safeguarding versus ransomware and malware.
CEO of Senetas, Andrew Wilson says, “Remote operate is right here to continue to be, but it is also presenting lots of alternatives for destructive actors. Sharing individual and economical information and facts more than e-mail is commonplace in legal, accounting and house loan broking products and services all around the entire world, with the stability of that info generally becoming an afterthought.”
For much more specifics: https://www.suredrop.io/
CylanceGUARD
Businesses of all sizes are challenged to set up insurance policies and protected info on a rising range of devices, major to an greater quantity of alerts to handle.
To assist solve this, BlackBerry delivers CylanceGUARD, an on-desire, 24/7/365 Managed Extended Detection and Response (XDR) support that works by using the prediction advantage of Artificial Intelligence (AI) to detect or remediate threats just before they result in damage.
Offered on a subscription, it is especially appealing for SMBs who benefit from organization-grade cybersecurity equipment and assist, at a portion of the expense.
CylanceGuard is obtainable to Australian businesses by using a amount of our MSSP companions in two unique packages, CylanceGUARD and CylanceGUARD Advanced, intended to meet any business’s wants.
Much more here.




