[ad_1]

Getty Visuals
Last year, Tesla issued an update that produced its motor vehicles much easier to start off just after becoming unlocked with their NFC crucial playing cards. Now, a researcher has revealed how the characteristic can be exploited to steal cars.
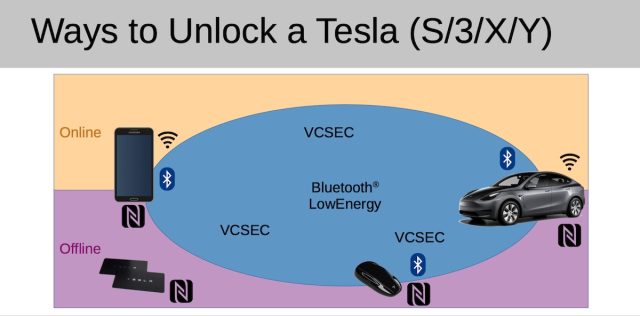
For years, drivers who applied their Tesla NFC important card to unlock their cars had to area the card on the center console to start off driving. Pursuing the update, which was noted in this article final August, drivers could run their autos instantly after unlocking them with the card. The NFC card is a person of a few usually means for unlocking a Tesla a key fob and a cell phone application are the other two.
https://trifinite.org/Downloads/20220604_tempa_presentation_recon22_public.pdf
Enrolling your very own crucial
Martin Herfurt, a protection researcher in Austria, quickly recognized something odd about the new element: Not only did it enable the auto to quickly get started inside 130 seconds of currently being unlocked with the NFC card, but it also put the auto in a condition to take entirely new keys—with no authentication expected and zero indication offered by the in-vehicle exhibit.
“The authorization supplied in the 130-2nd interval is far too standard… [it’s] not only for generate,” Herfurt claimed in an on-line interview. “This timer has been launched by Tesla… in get to make the use of the NFC card as a principal indicates of using the motor vehicle far more convenient. What must take place is that the automobile can be began and driven without the need of the person owning to use the vital card a second time. The dilemma: within just the 130-next period of time, not only the driving of the car or truck is approved, but also the [enrolling] of a new important.”
The official Tesla cellular phone app will not permit keys to be enrolled unless it can be connected to the owner’s account, but irrespective of this, Herfurt observed that the car gladly exchanges messages with any Bluetooth Lower Vitality, or BLE, device that is nearby. So the researcher designed his individual application, named Teslakee, that speaks VCSec, the exact same language that the formal Tesla application utilizes to communicate with Tesla vehicles.
A destructive variation of Teslakee that Herfurt intended for evidence-of-strategy functions demonstrates how simple it is for intruders to surreptitiously enroll their own crucial through the 130-2nd interval. (The researcher programs to release a benign edition of Teslakee inevitably that will make this kind of assaults tougher to have out.) The attacker then works by using the Teslakee application to trade VCSec messages that enroll the new important.
All that is needed is to be within assortment of the vehicle in the course of the important 130-2nd window of it being unlocked with an NFC card. If a motor vehicle operator normally uses the cellular phone app to unlock the car—by much the most typical unlocking approach for Teslas—the attacker can power the use of the NFC card by using a signal jammer to block the BLE frequency used by Tesla’s mobile phone-as-a-crucial application.
This video clip demonstrates the attack in action:
https://www.youtube.com/check out?v=yfG4JS71eUY
Absent in less than 130 Seconds.
As the driver enters the car or truck soon after unlocking it with an NFC card, the thief commences exchanging messages in between the weaponized Teslakee and the motor vehicle. Ahead of the driver has even driven away, the messages enroll a key of the thief’s alternative with the auto. From then on, the thief can use the essential to unlock, commence, and convert off the automobile. There is no indication from the in-car show or the reputable Tesla application that just about anything is amiss.
Herfurt has correctly made use of the assault on Tesla Styles 3 and Y. He has not examined the system on new 2021+ facelift designs of the S and X, but he presumes they are also vulnerable for the reason that they use the same indigenous aid for mobile phone-as-a-key with BLE.
Tesla did not answer to an e-mail in search of remark for this publish.



