[ad_1]

Getty Photographs
Scientists have determined stealthy new malware that threat actors have been making use of for the earlier 15 months to backdoor Microsoft Trade servers following they have been hacked.
Dubbed SessionManager, the destructive computer software poses as a genuine module for Net Information and facts Products and services (IIS), the net server installed by default on Trade servers. Companies frequently deploy IIS modules to streamline specific procedures on their world wide web infrastructure. Scientists from protection company Kaspersky have identified 34 servers belonging to 24 companies that have been contaminated with SessionManager considering that March 2021. As of previously this month, Kaspersky claimed, 20 corporations remained contaminated.
Stealth, persistence, power
Destructive IIS modules offer you an suitable implies to deploy highly effective, persistent, and stealthy backdoors. Once put in, they will answer to specifically crafted HTTP requests sent by the operator instructing the server to obtain email messages, increase further more malicious access, or use the compromised servers for clandestine uses. To the untrained eye, the HTTP requests glance unremarkable, even even though they give the operator total command above the equipment.
“Such destructive modules ordinarily hope seemingly respectable but precisely crafted HTTP requests from their operators, induce steps primarily based on the operators’ hidden instructions if any, then transparently go the ask for to the server for it to be processed just like any other ask for,” Kaspersky researcher Pierre Delcher wrote. “As a result, this kind of modules are not effortlessly noticed by regular checking tactics: they do not essentially initiate suspicious communications to external servers, receive commands via HTTP requests to a server that is precisely exposed to this sort of procedures, and their documents are generally put in neglected destinations that comprise a large amount of other reputable files.”
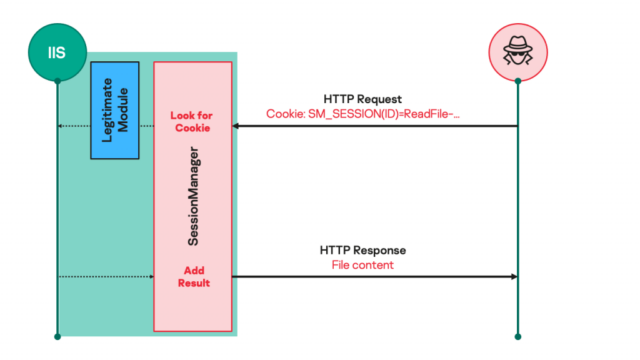
Kaspersky
At the time SessionManager is deployed, operators use it to profile the infected atmosphere even more, acquire passwords stored in memory, and install extra applications, which includes a PowerSploit-dependent reflective loader, Mimikat SSP, ProcDump, and a legitimate Avast memory dump software. Kaspersky acquired a number of SessionManager variants that date again to at least March 2021. The samples show a constant evolution that has extra a lot more capabilities with each individual new model. The most recent variation of the malicious module contains the following:
Command title
(SM_SESSION cookie benefit)Command parameters
(supplemental cookies)Involved functionality GETFILE FILEPATH: path of file to be read. FILEPOS1: offset at which to start out examining, from file start. FILEPOS2: greatest quantity of bytes to read through.
Read the content of a file on the compromised server and mail it to the operator as an HTTP binary file named great.rar. PUTFILE FILEPATH: path of file to be composed. FILEPOS1: offset at which to start off crafting.
FILEPOS2: offset reference.
FILEMODE: asked for file obtain variety.
Compose arbitrary content material to a file on the compromised server. The info to be written in the specified file is passed inside the HTTP ask for overall body. DELETEFILE FILEPATH: path of file to be deleted. Delete a file on the compromised server. FILESIZE FILEPATH: route of file to be calculated. Get the sizing (in bytes) of the specified file. CMD None. Run an arbitrary course of action on the compromised server. The system to run and its arguments are specified in the HTTP ask for overall body working with the structure: t . The typical output and error knowledge from system execution are despatched back as plain textual content to the operator in the HTTP response physique. PING None. Look at for SessionManager deployment. The “Wokring OK” (sic.) message will be sent to the operator in the HTTP response human body. S5Hook up S5HOST: hostname to hook up to (special with S5IP). S5PORT: offset at which to commence writing.
S5IP: IP deal with to hook up to if no hostname is offered (distinctive with S5HOST).
S5TIMEOUT: highest hold off in seconds to make it possible for for relationship.
Connect from compromised host to a specified network endpoint, using a produced TCP socket. The integer identifier of the developed and connected socket will be returned as the benefit of the S5ID cookie variable in the HTTP response, and the status of the relationship will be described in the HTTP reaction system. S5Generate S5ID: identifier of the socket to generate to, as returned by S5Hook up. Publish knowledge to the specified connected socket. The facts to be penned in the specified socket is handed inside of the HTTP ask for body. S5Browse S5ID: identifier of the socket to read from, as returned by S5Join. Browse information from the specified connected socket. The examine knowledge is despatched back within the HTTP reaction body. S5Near S5ID: identifier of the socket to close, as returned by S5Connect. Terminate an present socket connection. The status of the procedure is returned as a message in the HTTP response entire body.
Recall ProxyLogon?
SessionManager receives put in immediately after risk actors have exploited vulnerabilities acknowledged as ProxyLogon in just Microsoft Trade servers. Kaspersky has identified it infecting NGOs, governments, militaries, and industrial companies in Africa, South The usa, Asia, and Europe.
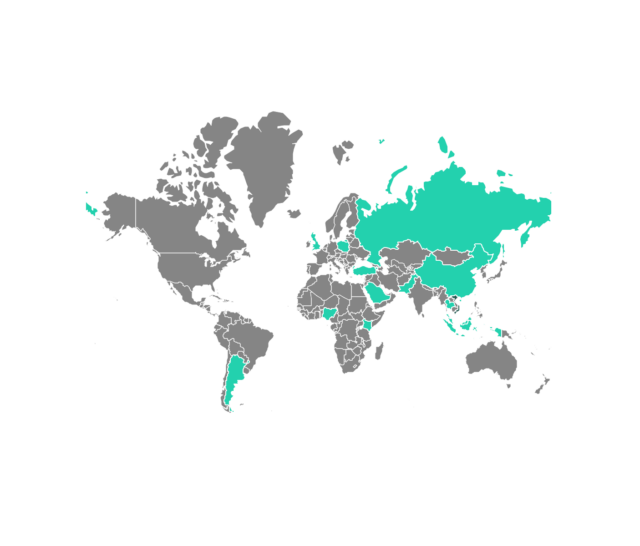
Kaspersky
Kaspersky reported it has medium-to-high self confidence that a previously discovered threat actor that scientists contact Gelsemium has been deploying SessionManager. Stability agency ESET posted a deep dive on the team (PDF) previous calendar year. Kaspersky’s attribution is dependent on the overlap of code applied by the two groups and victims qualified.
Disinfecting servers that have been hit by SessionManager or equivalent malicious IIS modules is a challenging process. Kaspersky’s publish is made up of indicators that corporations can use to decide if they’ve been contaminated and actions they should take in the party they’ve been infected.


