[ad_1]

Scientists have unearthed a discovery that does not manifest all that usually in the realm of malware: a experienced, by no means-in advance of-witnessed Linux backdoor that makes use of novel evasion methods to conceal its presence on contaminated servers, in some situations even with a forensic investigation.
On Thursday, scientists from Intezer and The BlackBerry Threat Investigate & Intelligence Group stated that the earlier undetected backdoor combines significant concentrations of access with the skill to scrub any indicator of an infection from the file technique, technique procedures, and community visitors. Dubbed Symbiote, it targets economic establishments in Brazil and was very first detected in November.
Researchers for Intezer and BlackBerry wrote:
What helps make Symbiote diverse from other Linux malware that we usually appear across, is that it desires to infect other working processes to inflict injury on infected devices. As a substitute of being a standalone executable file that is run to infect a device, it is a shared item (SO) library that is loaded into all operating processes employing LD_PRELOAD (T1574.006), and parasitically infects the equipment. Once it has infected all the operating processes, it offers the risk actor with rootkit performance, the capability to harvest credentials, and remote entry ability.
With the help of LD_PRELOAD, Symbiote will load right before any other shared objects. That will allow the malware to tamper with other library information loaded for an software. The picture below reveals a summary of all of the malware’s evasion tactics.
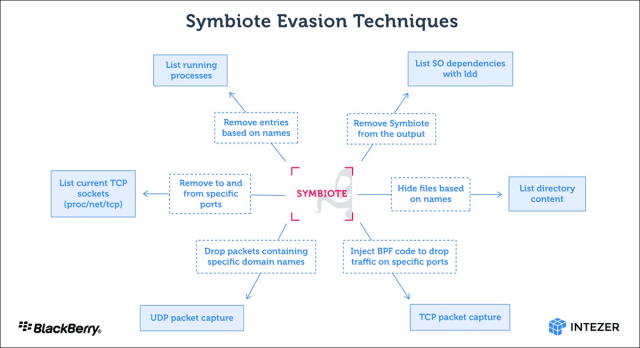
BPF in the graphic refers to the Berkeley Packet Filter, which will allow men and women to conceal malicious network site visitors on an infected equipment.
“When an administrator starts off any packet seize device on the contaminated machine, BPF bytecode is injected into the kernel that defines which packets need to be captured,” the researchers wrote. “In this procedure, Symbiote adds its bytecode to start with so it can filter out network targeted traffic that it doesn’t want the packet-capturing software program to see.”
A single of the stealth strategies Symbiote employs is identified as libc operate hooking. But the malware also employs hooking in its position as a facts-theft device. “The credential harvesting is performed by hooking the libc examine operate,” the researchers wrote. “If an ssh or scp method is calling the functionality, it captures the qualifications.”
So significantly, there’s no proof of bacterial infections in the wild, only malware samples discovered on line. It’s unlikely this malware is commonly lively at the instant, but with stealth this robust, how can we be confident?




