[ad_1]

Aurich Lawson | Getty Illustrations or photos
A large flood of malicious targeted visitors that not long ago established a new distributed denial-of-service document came from an not likely supply. A botnet of just 5,000 products was liable, as extortionists and vandals keep on to establish at any time much more strong attacks to knock websites offline, stability scientists reported.
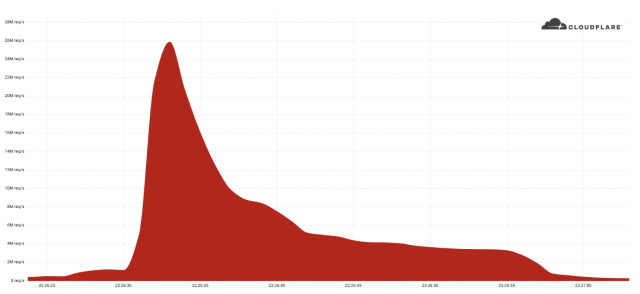
The DDoS sent 26 million HTTPS requests per next, breaking the preceding history of 15.3 million requests for that protocol set only 7 weeks back, Cloudflare Solution Manager Omer Yoachimik documented. Contrary to far more common DDoS payloads such as HTTP, SYN, or SYN-ACK packets, destructive HTTPS requests involve considerably much more computing assets for the attacker to deliver and for the defender or victim to take up.
4,000 periods more powerful
“We’ve seen really significant assaults in the past about (unencrypted) HTTP, but this attack stands out because of the assets it demanded at its scale,” Yoachimik wrote.
Cloudflare
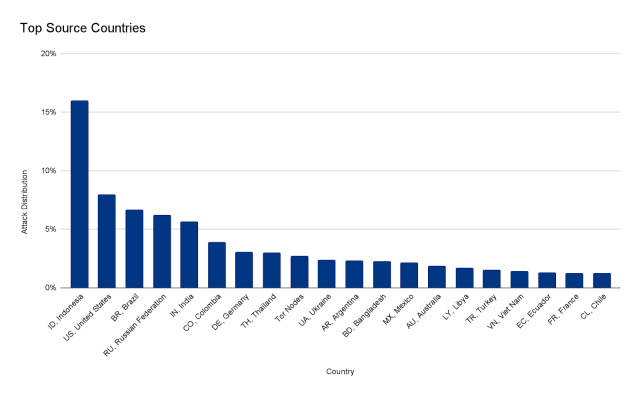
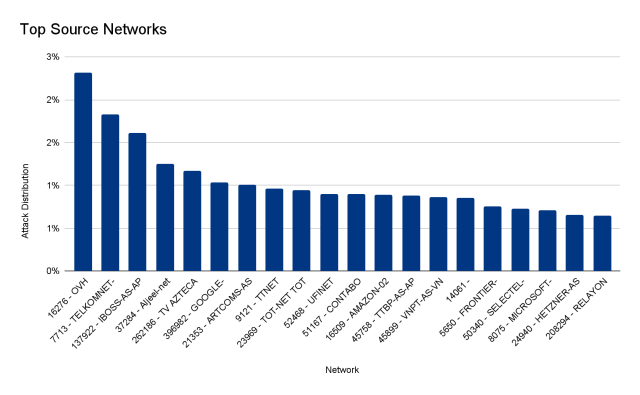
The burst lasted significantly less than 30 seconds and created much more than 212 million HTTPS requests from more than 1,500 networks in 121 nations around the world, with Indonesia, the United States, Brazil, and Russia topping the checklist. The top rated networks utilised incorporated French-based OVH (Autonomous Method Amount 16276), the Indonesian Telkomnet (ASN 7713), the US-centered iboss (ASN 137922), and the Libyan Ajeel (ASN 37284). About 3 per cent of the assault came by way of Tor nodes.
Cloudflare
Cloudflare
As was the scenario with the prior 15.3 million-HTTPS-requests-for each-second assault, the new a person originated predominantly on devices from cloud service vendors. The servers and digital devices available from these vendors are noticeably additional highly effective than compromised pcs and IoT equipment linked to household ISPs, which are the extra popular supply of DDoSes.
Yoachimik wrote:
The 26M rps DDoS attack originated from a compact but impressive botnet of 5,067 units. On ordinary, each and every node produced around 5,200 rps at peak. To contrast the dimensions of this botnet, we’ve been tracking another a great deal greater but significantly less potent botnet of in excess of 730,000 units. The latter, more substantial botnet was not equipped to generate more than a person million requests for each next, i.e. around 1.3 requests for each 2nd on typical per unit. Placing it plainly, this botnet was, on average, 4,000 times much better due to its use of virtual machines and servers.
In some conditions, DDoSers merge their use of cloud-based mostly devices with other methods to make their assaults more strong. In the 15.3 million-HTTPS-requests-for each-next DDoS from before this 12 months, for illustration, Cloudflare uncovered proof that the risk actors might have exploited a significant vulnerability. This exploit permitted them to bypass authentication in a large assortment of Java-primarily based applications employed within the cloud environments operating their assault devices.
DDoS assaults can be measured in numerous ways, like by the quantity of details, the range of packets, or the quantity of requests sent every second. The other present-day documents are 3.4 terabits for every next for volumetric DDoSes—which endeavor to take in all bandwidth out there to the target—and 809 million packets for each next. The 26 million HTTPS requests for every second split the former 17.2 million-requests-for every-next history established in 2020. Not only did that previously assault provide much less packets than the new file, but it also relied on HTTP, which is just not as potent as HTTPS.
The Cloudflare item supervisor reported that his enterprise instantly detected and mitigated the assault from the shopper, which was utilizing Cloudflare’s free of charge provider.


