[ad_1]

An unusually state-of-the-art hacking group has spent just about two many years infecting a extensive variety of routers in North The united states and Europe with malware that usually takes comprehensive manage of linked units managing Windows, macOS, and Linux, researchers claimed on Tuesday.
So considerably, researchers from Lumen Technologies’ Black Lotus Labs say they’ve recognized at minimum 80 targets contaminated by the stealthy malware, infecting routers built by Cisco, Netgear, Asus, and DayTek. Dubbed ZuoRAT, the remote obtain Trojan is portion of a broader hacking marketing campaign that has existed due to the fact at the very least the fourth quarter of 2020 and carries on to work.
A significant stage of sophistication
The discovery of tailor made-built malware created for the MIPS architecture and compiled for smaller workplace and household business routers is considerable, particularly provided its assortment of abilities. Its capacity to enumerate all equipment connected to an contaminated router and accumulate the DNS lookups and network traffic they send and acquire and keep on being undetected is the hallmark of a really subtle menace actor.
“Even though compromising SOHO routers as an accessibility vector to acquire access to an adjacent LAN is not a novel method, it has rarely been documented,” Black Lotus Labs scientists wrote. “In the same way, experiences of person-in-the-middle fashion attacks, these types of as DNS and HTTP hijacking, are even rarer and a mark of a elaborate and qualified operation. The use of these two strategies congruently shown a substantial stage of sophistication by a menace actor, indicating that this campaign was possibly done by a condition-sponsored firm.”
The campaign comprises at least four parts of malware, three of them created from scratch by the threat actor. The very first piece is the MIPS-based ZuoRAT, which carefully resembles the Mirai Online of Items malware that achieved document-breaking dispersed denial-of-support attacks that crippled some World wide web products and services for days. ZuoRAT normally receives installed by exploiting unpatched vulnerabilities in SOHO products.
As soon as installed, ZuoRAT enumerates the gadgets related to the contaminated router. The risk actor can then use DNS hijacking and HTTP hijacking to cause the linked products to install other malware. Two of those malware pieces—dubbed CBeacon and GoBeacon—are personalized-built, with the initial penned for Windows in C++ and the latter composed in Go for cross-compiling on Linux and macOS equipment. For flexibility, ZuoRAT can also infect linked equipment with the greatly utilized Cobalt Strike hacking tool.
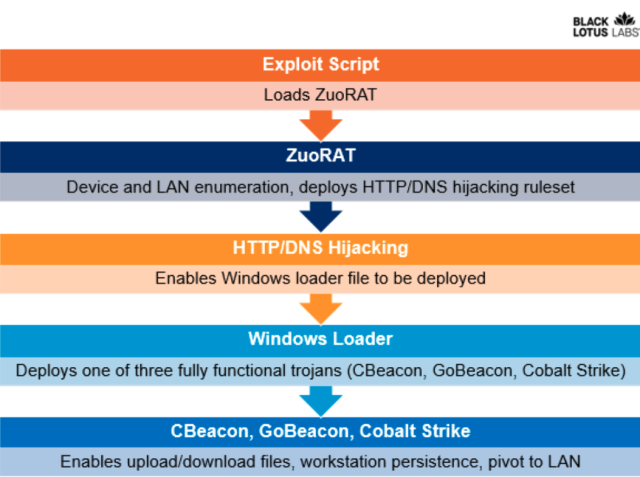
ZuoRAT can pivot bacterial infections to linked gadgets working with 1 of two solutions:
- DNS hijacking, which replaces the legitimate IP addresses corresponding to a area these types of as Google or Facebook with a malicious just one operated by the attacker.
- HTTP hijacking, in which the malware inserts by itself into the relationship to make a 302 error that redirects the user to a various IP address.
Deliberately sophisticated
Black Lotus Labs stated the command and manage infrastructure utilized in the campaign is intentionally complicated in an attempt to conceal what’s occurring. A person established of infrastructure is utilised to command infected routers, and one more is reserved for the connected units if they’re later infected.
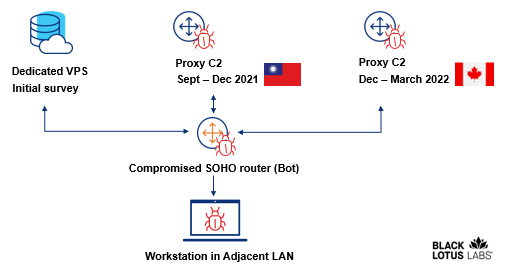
The scientists noticed routers from 23 IP addresses with a persistent relationship to a manage server that they think was executing an first survey to determine if the targets were being of desire. A subset of all those 23 routers later interacted with a Taiwan-centered proxy server for a few months. A even further subset of routers rotated to a Canada-centered proxy server to obfuscate the attacker’s infrastructure.
This graphic illustrates the measures detailed included.
The menace actors also disguised the landing web site of a management server to glance like this:
The researchers wrote:
Black Lotus Labs visibility suggests ZuoRAT and the correlated exercise symbolize a hugely targeted campaign in opposition to US and Western European businesses that blends in with common web traffic through obfuscated, multistage C2 infrastructure, most likely aligned with multiple phases of the malware an infection. The extent to which the actors take pains to cover the C2 infrastructure are not able to be overstated. Initially, to stay clear of suspicion, they handed off the preliminary exploit from a devoted digital non-public server (VPS) that hosted benign written content. Following, they leveraged routers as proxy C2s that hid in basic sight by way of router-to-router interaction to even more keep away from detection. And eventually, they rotated proxy routers periodically to avoid detection.
The discovery of this ongoing marketing campaign is the most critical one influencing SOHO routers considering the fact that VPNFilter, the router malware established and deployed by the Russian federal government that was discovered in 2018. Routers are generally ignored, specially in the do the job-from-dwelling era. When companies usually have rigid needs for what devices are authorized to hook up, number of mandate patching or other safeguards for the devices’ routers.
Like most router malware, ZuoRAT won’t be able to endure a reboot. Only restarting an contaminated machine will eliminate the preliminary ZuoRAT exploit, consisting of information saved in a short term listing. To absolutely get better, nonetheless, contaminated products must be factory reset. Sad to say, in the function linked units have been infected with the other malware, they are not able to be disinfected so conveniently.




